Both EU and US Signal They Can’t Help Business Against Today’s Threats
In a historic set of statements, both Europe and the U.S. are reinforcing the idea that businesses are extremely vulnerable to nation-state hacking. Homeland Security Secretary Kirstjen Nielsen said recently, We are under siege from transnational criminals…faceless cyber thugs and hackers…and resurgent nation-state rivals.” She continued, “America is not prepared for this. Your average private citizen or company is no match against a nation-state such as China, Iran, North Korea, or Russia. It is not a fair fight. And until now our government has done far too little to back them up.” She concluded, “The agency’s overall plan, including cybersecurity, is to integrate its strategies and initiatives across agencies and offices in a more unified approach.”
What the U.S. lacks in the country’s cyber defenses is an understanding of emerging threats, according to Nielsen. “Failure to look at the future or limiting our thinking based on what we’ve observed in the past, those in and of themselves are risks,” she said. “What worries me, though, is not what these threat actors have done, but what they have the capability to do. The possibilities are limitless,” she said. In particular, Nielsen pointed to “forward deployed” supply chain attacks, in which U.S. adversaries use state-owned companies to launch insider attacks.
President Trump’s fiscal 2020 budget proposal calls for nearly $11 billion to be set aside for cybersecurity, most of which would go to the Department of Defense (DoD) and Homeland Security’s initiatives and operations. Under the Administration’s budget proposal some $9.6 billion for cybersecurity would be allocated to the DOD.
In the meantime, law enforcement agencies across the EU are preparing for major cross-border attacks.
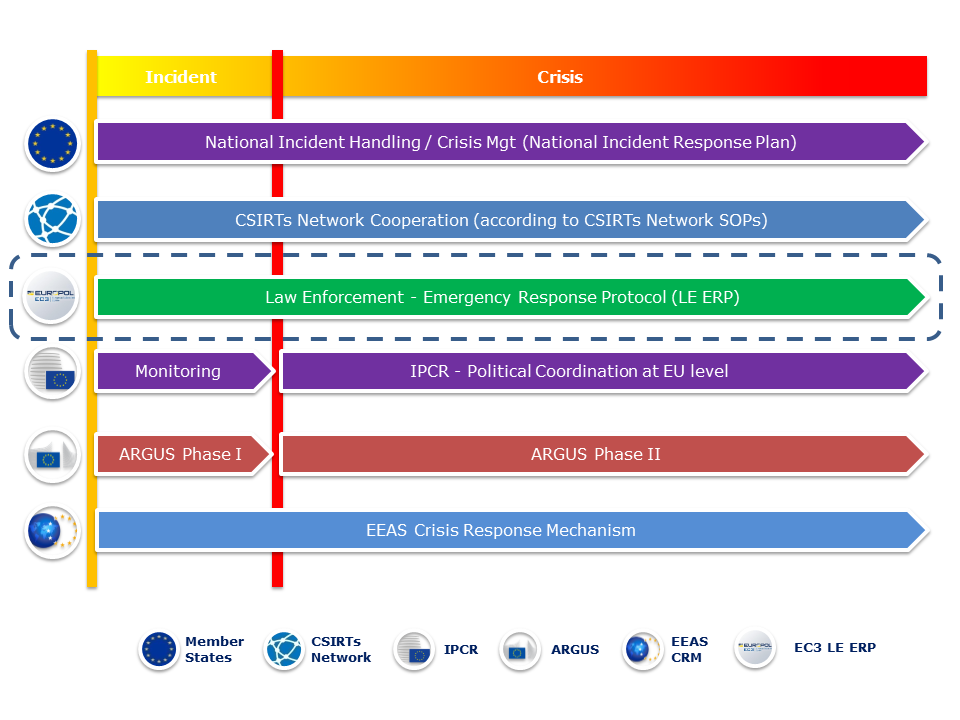
In other words, they have put into place, a plan which they hope will result in less cyberattacks.
In a Europol press release they stated, “In 2017, the unprecedented WannaCry and NotPetya cyber-attacks underlined the extent to which incident-driven and reactive responses were insufficient to address rapidly evolving cybercriminal modus operandi effectively.”
To prepare for major cross-border cyber-attacks, an EU Law Enforcement Emergency Response Protocol has been adopted by the Council of the European Union. The Protocol gives a central role to Europol’s European Cybercrime Centre (EC3) and is part of the EU Blueprint for Coordinated Response to Large-Scale Cross-Border Cybersecurity Incidents and Crises. It serves as a tool to support the EU law enforcement authorities in providing immediate response to major cross-border cyber-attacks through rapid assessment, the secure and timely sharing of critical information and effective coordination of the international aspects of their investigations.
The EU Law Enforcement Emergency Response Protocol determines the procedures, roles and responsibilities of key players both within the EU and beyond; secure communication channels and 24/7 contact points for the exchange of critical information; as well as the overall coordination and de-confliction mechanism. It strives to complement the existing EU crisis management mechanisms by streamlining transnational activities and facilitating collaboration with the relevant EU and international players, making full use of Europol’s resources. It further facilitates the collaboration with the network and information security community and relevant private sector partners.
In order to establish the criminal nature of an attack, first responders perform all required measures in a way to preserve the electronic evidence that could be found within the IT systems affected by the attack, which are essential for any criminal investigation or judicial procedure.
The protocol is a multi-stakeholder process and entails in total, seven possible core stages from the early detection and the threat classification to the closure of the Emergency Response Protocol.
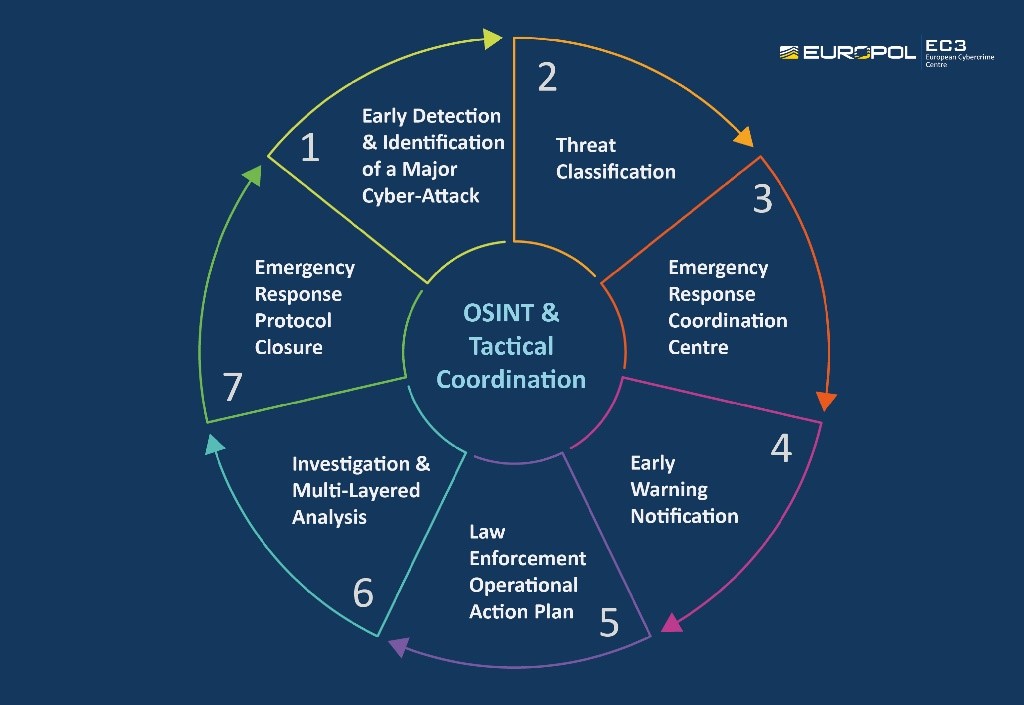
This is Europe’s response to a threat like NotPetya which we were first to report was malware which exceeded $10 billion in damages – just by tallying public filings alone. Even worse, because it was considered a hostile or warlike action, the insurance company refused to pay.
It is unclear what impact if any EC3 would have had on such attacks. In other words, let’s say we were three years into EC3 being fully implemented and NotPetya 2.0 was unleashed the same way as NotPetya. Via an infected Ukrainian tax site and phishing attacks. How could they stop it?
By more effectively preserving electronic information?
How does this help a company with $500 million in now-useless computer systems?
Companies seem to be exactly as vulnerable with EC3 in the mix as they were before NotPetya first reared its ugly head.
The U.S. plans to spend billions but on what? They already spend a great deal but this hasn’t revered the trend of cyberattack growth.
The message can’t be any clearer. The EU and US are loudly telling us they can’t help business against cyber-attacks. Not major ones anyway.
And the pace of any governmental action is absolutely glacial. Hackers are innovating and outspending us ten-to-one already. How can a centralized government ever stay ahead of such a decentralized threat with actors able to collaborate anonymously via the dark web? All the innovation such as cloud and aaS which tech startups enjoy today are also being used by global hackers… They can access botnets of millions of infected machines and lease out any malicious service they like.
It is truly a scary time to be a corporation.
The reality is sad but true. Unless the western world says they will be retaliating with physical attacks to ones which are cyber in nature, what do nation-state hackers care if the EC3 documents how they attacked a western company?
Moreover, Russia is said to have been responsible for NotPetya. Armed with this information, what has it changed? Russia isn’t paying for any of the damaged computers or loss of profits.
In short, all companies need to do the best they can to protect themselves from attacks before they happen. Sure, nation-state hackers are better armed than corporations but the best any entity can and should do is to shore up its defenses to present a more resilient target to the outside world. In this manner, the goal is to persuade the attacker that there are easier targets out there to disable or infiltrate.
Every company is a potential target and should use a phishing simulation tool which tests employees by sending safe phishing emails. When employees click, they are then presented with educational material which helps them learn what to avoid.
Some solutions are so effective, they can achieve over a 90% click-rate. The good news is, the workers who click, can be quickly trained on what to avoid in the future.
Here are other areas all organizations looking to promote a cybersecurity culture need to focus on:
- Cybersecurity training must be done regularly.
- Auditing and documentation must be performed regularly to ensure systems are secure.
- Anomaly detection should be running constantly to detect threats as they emerge.
- Penetration testing shows if systems can easily be reached from the outside. Here is a case where this test might have saved two company’s’ reputations from being destroyed.
- Network forensics for when a breach eventually occurs. The bad guys always seem to get in eventually.
- An action plan to follow when a breach does occur. Once it happens, few will have the clear heads needed to “wing it” correctly. Equifax botched it’s response in what is being called a PR catastrophe.
To ensure your organization is safe – even if you have internal IT, hire an experienced MSP or MSSP.



